A complete guide to remote access technology, benefits, and security

Remote access (sometimes referred to as “remote desktop” or "remote desktop connection") is simply the ability to access a device from another device, at any time, and from anywhere. With remote access, a user can control all the files and applications on another device as if the user was actually sitting in front of it. Remote access can be used across devices to enable remote PC access, remote Mac access, remote iPhone access, and more.
Two common examples
Why is remote access important?
Computing doesn’t just happen at work or at home anymore but can happen from anywhere on different devices with different operating systems. Remote access software makes computing more flexible in terms of where and when work and other digitally enabled activities can get done. For businesses that want to work flexibly (i.e., all businesses), it’s simply foundational to have software in place to enable remote access technologies such as:
If your business has remote customers and/or employees, you’ll need to support them from where they are and on any device. For example, what happens when an online customer using a home desktop wants to buy from you, but confronts technical difficulties? Or an employee working from home can’t access a company system or customer data she needs to do her work? Lost sales and productivity costs money.
In either scenario, remotely accessing the customer or employee’s computer gives your IT support team the ability to fix an issue and avoid financial losses to your business. Remote access tools thus enable business continuity, while driving both customer and employee experience.
Employees need remote access too. Whether they’re working from home under a remote or hybrid work arrangement or traveling for business, employees must have the ability to access work systems to get work done remotely. Without remote desktop access, they’d only be able to work by showing up in the physical office, which may have been okay in 1998 but isn’t any longer in today’s more flexible, mobile business climate.
While not all the same, remote desktop solutions address the same function. Three aspects are involved:
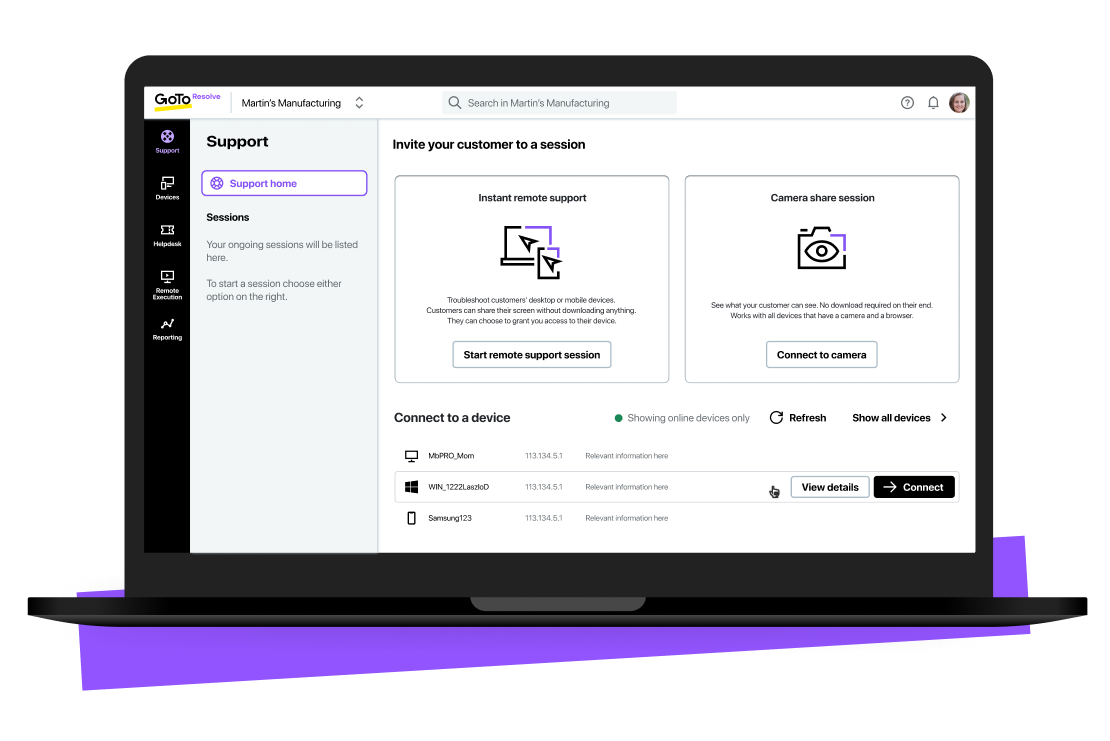
For most remote access technologies, you’ll need to have already downloaded and installed the remote access software/application onto any device you intend to remote to and onto any device you want to remote from. Once the software/apps are installed, you can just open the app on the device you’re remoting from (the device in front of you) and connect to the device you want to remote to (maybe a desktop in your far-away office). However, for ad hoc remote support use cases, some solutions (like GoTo Resolve) do not require any downloads on the end user’s device for a technician to remotely access that device. The entire process is web-based.
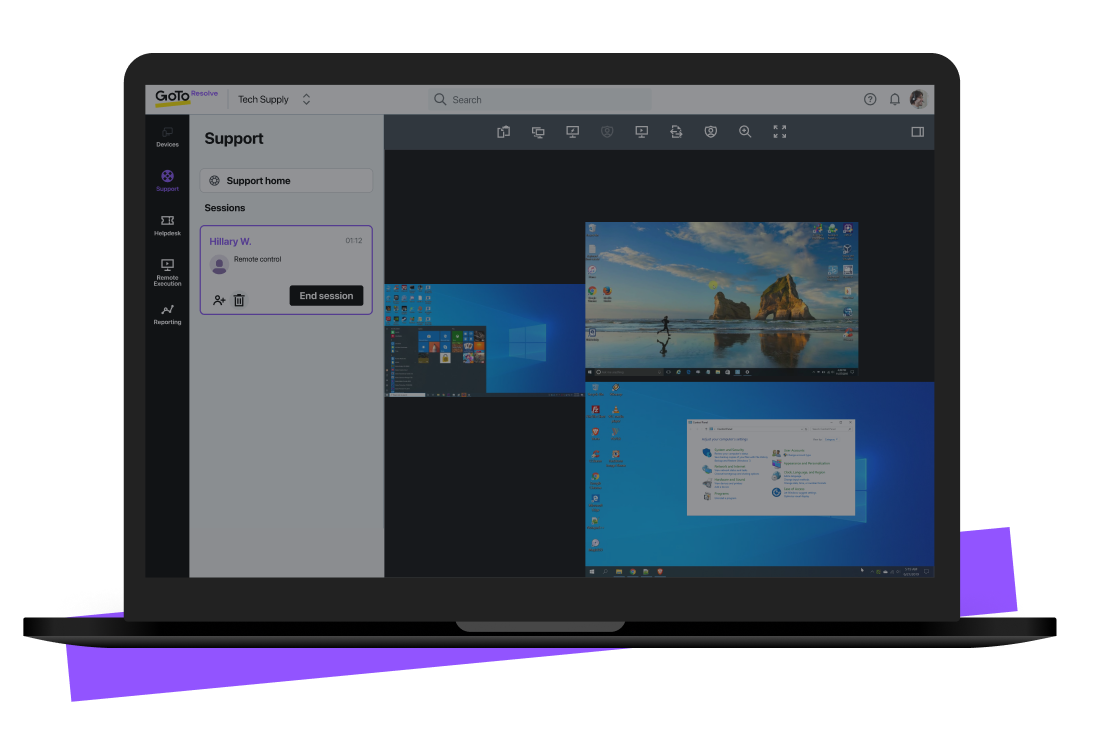
Say Carol needs access to an important, customer-related file on her office desktop in Miami, but she’s representing her company at a technology conference in San Francisco. With remote computer access, Carol can just pull out her iPhone, open her remote access mobile app, and quickly connect to her office desktop in Miami to open the customer-related file. She can even edit, save, email, or transfer the file in question to the IPhone she’s remoting from.
Now if Carol was on your IT support team, and she was attending the conference, we’d have a different use case. She could remotely access a user’s computer in the company’s main office (or the user’s home) in order to resolve the user’s pending IT issues. She could even gain unattended access remotely, meaning Carol could fix a user's issue even if the user isn't in front of their device. In all of these scenarios, Carol is efficiently and securely doing her work from a remote location using a device in front of her that can connect to another device.
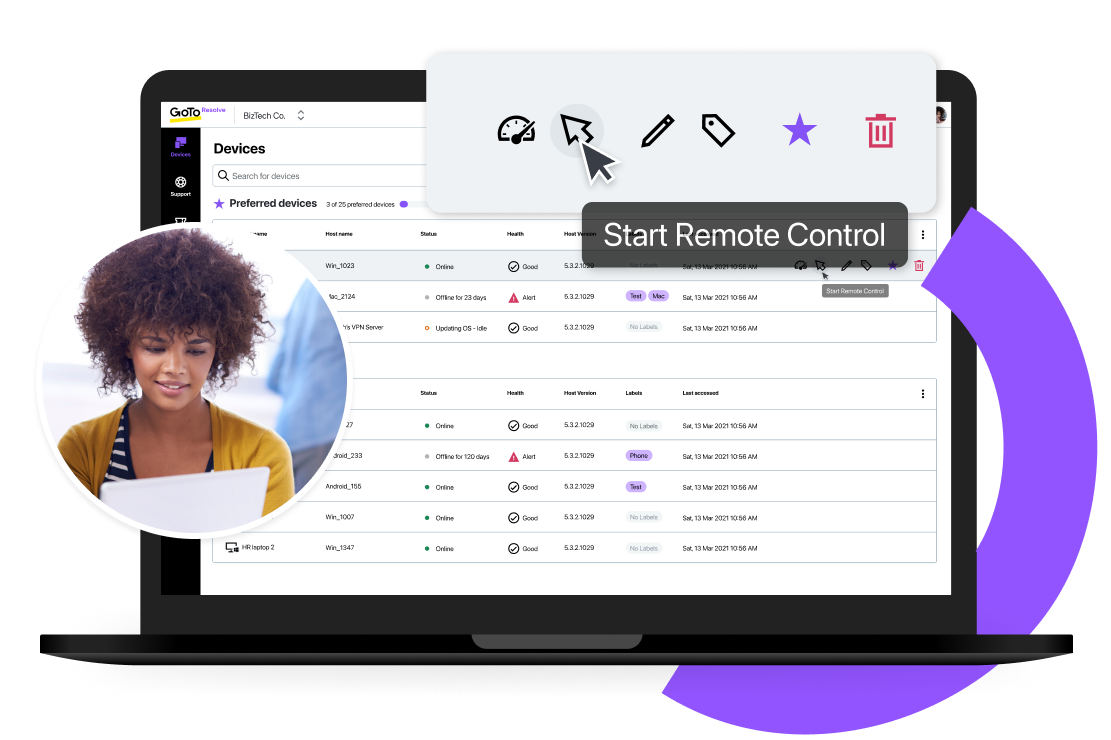
Let’s dig into the technologies that make remote access possible. There are three typically used types of remote access:
Now let's get a little more specific. Here are some of the most commonly used types of remote access connections:
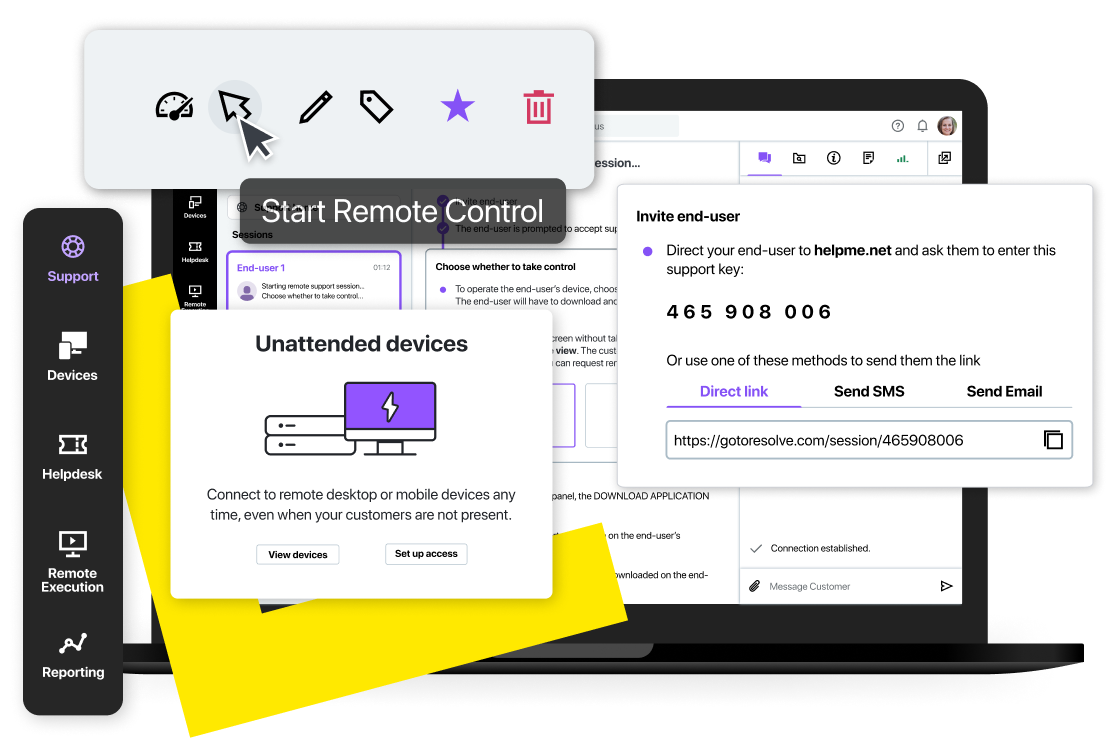
Any size business will benefit from having remote access capability. Here are half a dozen of the many benefits:




IT leaders like you already understand quite well the growing cyberthreats out there, as a recent IDG report makes clear:
Potential damage and risk is high. It would be difficult to overestimate the importance of having secure remote access connections.

If malicious actors were able to access your remote connections, they could steal and compromise sensitive customer, employee, and proprietary data. Not only would this pose a significant, even existential, risk to your organization’s image, it would also subject you to extortion/ransomware attacks, regulatory penalties, and could destroy both your customer and employee experiences. That’s a lot of risk you need to mitigate.

Cyberthreats are increasing. You’ve likely read about many of the most common security risks and threats in the media, including ransomware attacks, denial-of-service attacks, malicious actors hacking into remote support sessions, theft of sensitive and/or financial data, and worse. Cyberthreats just keep growing in sophistication, especially as malicious actors have easy access to emerging technologies such as AI. As hackers up their game, your IT team needs to up its cybersecurity defense, including securing remote access connections.
Fortunately, great security tools currently exist for securing remote access, and here are some of them:
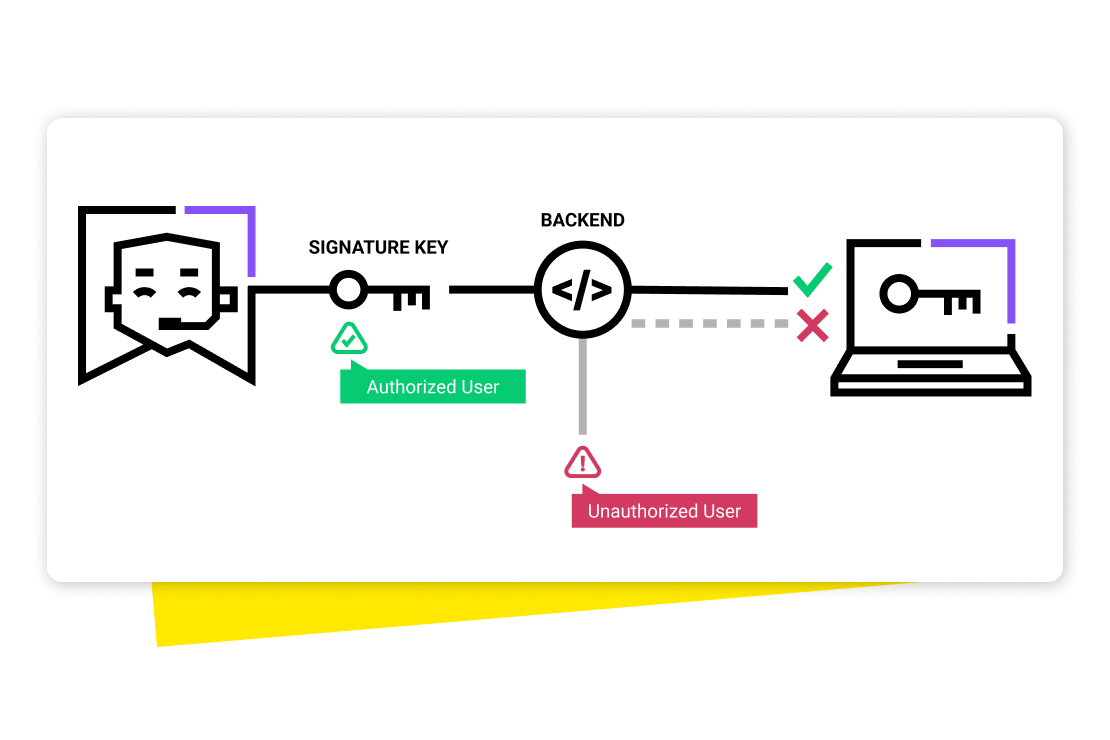
Let’s look at the top remote access best practices that can help you optimize the technology for your organization:
Simply by reading this guide, you’re already way ahead of most IT people in understanding how remote access works. Like any technology, remote access must be widely adopted and learned by your people to gain its maximum benefits. It is the role of the organization and its leadership team to make necessary investments in training and ensuring that people are using remote access efficiently.
You can’t just introduce remote access without training and guidelines to ensure it’s been used well (see below for more on this).
Once training and guidelines are in place, you’re far from finished. You’ll need to measure and monitor how your people are actually using their remote access capabilities. Any missteps, especially around security, can sacrifice the benefits. Set up structures to monitor and review how your people are using remote access and make any necessary adjustments in training or guidelines based on this incoming performance data.
By the way, tools like remote access with GoTo Resolve give administrators easy access to this kind of performance data.
Security will always be a top priority when it comes to remote access capabilities. By having the remote access security features we described in detail above, especially zero trust security, you’re in a better position to avoid and mitigate potential security threats.
Just as security is a special focus of your training efforts and guidelines around remote access, it should also be an independent focus of your performance monitoring efforts. Set up structured security audits, analyze the results, and make necessary adjustments. Lather, rinse, and repeat.
It’s important to be intentional about how your people use remote access capabilities. Your organization should develop a formalized approach in writing to remote access, describing exactly who can do what and when as well as detailing who can see what information/data and for what purposes. Share this policy with your people, train them on it, and when you make necessary policy adjustments, update your training and communications too.
Remote access solutions ensure business continuity and employee productivity for small and midsized businesses. Since these organizations don’t have the unlimited resources of enterprise-sized companies and their massive IT budgets, remote access becomes an essential lever for SMBs to “do more with less.”
The benefits of remote access for small business, similar to the benefits for behemoth Fortune 500 enterprises, include enabling remote and hybrid work, better customer and employee experiences, improved IT support operations, increased data and digital security/compliance, cost efficiencies, and much more.
No matter how big or small the organization in question, customers and employees alike demand the flexibility that remote access empowers.
If you want to enable flexible ways of engagement with people (customers and employees), you need remote access technologies. Remote access capabilities can help increase business productivity and efficiency, especially for your IT team in supporting your users.
Implementing remote access securely and effectively requires working with an experienced partner who will tailor any remote access solution to the specific needs of your business. GoTo Resolve makes remote access easy, so you can quickly bridge the gap between where you are today and where you want to go with your remote access strategy.